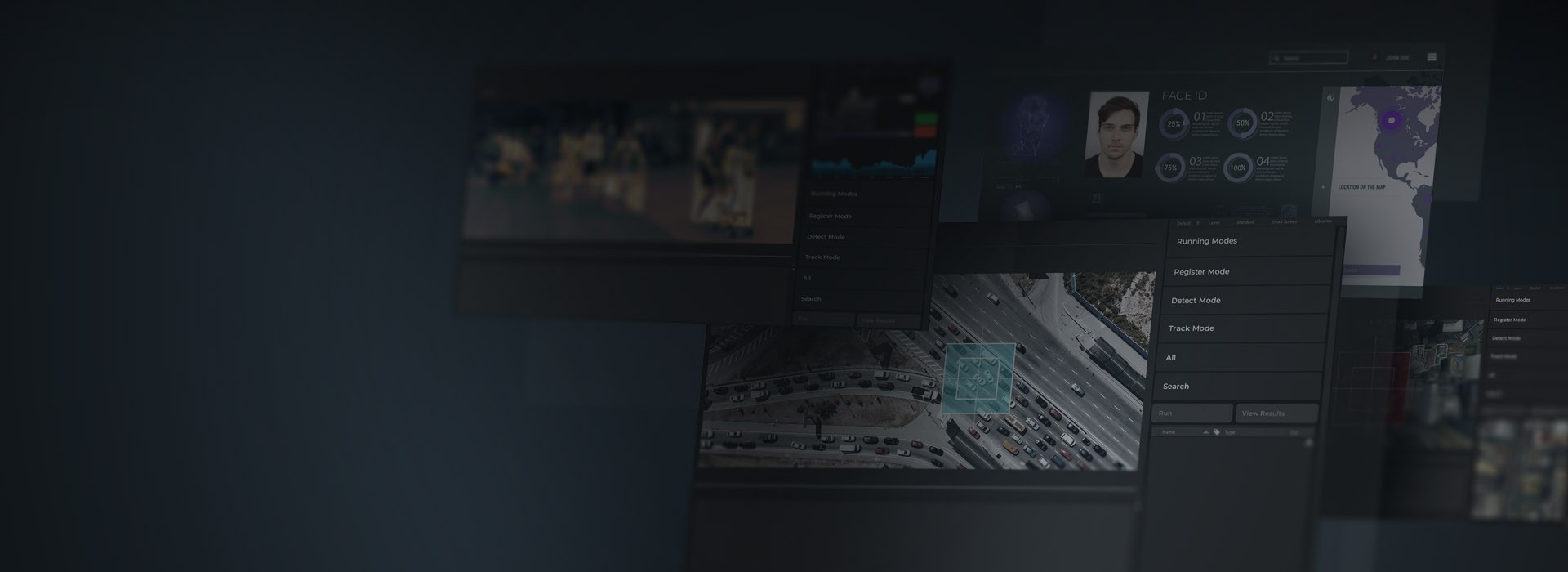
Advanced face recognition
- Real-time face recognition, identification, verification, and tracking
- Face images comparison against a database of persons of interest
- Multi-stage face detection to enhance discovery capabilities under challenging conditions
- Sophisticated head pose correction for frontal face image generation
- Accurate face spoofing and morphing detection
- Advanced face image post-processing