When it comes to providing value-based, patient-centered care, real-time video communication holds great promise in enabling healthcare systems to extend the reach, maximize efficiency, and improve clinical outcomes.
HIPAA-compliant video healthcare conferencing is essential in telemedicine, as it involves the electronic exchange of personal health data protected under the Health Insurance Portability and Accountability Act (HIPAA). With its Privacy and Security Rules, HIPAA requires healthcare providers to take the necessary steps to ensure confidentiality, integrity, and security of electronic protected health information (ePHI).
HIPAA prescribes relevant safeguards and controls — administrative, physical, and technical — to protect the flow of health data, while ensuring patients’ privacy and giving them greater control over their health information.
Recent data breaches in a major video conferencing platform, however, have raised a wave of concerns over privacy and security risks. After all, penalties for HIPAA non-compliance can be severe, reaching $250,000 for violation, not to mention the damage to a healthcare organization’s reputation, loss of patient trust, and decreased patient volume. Choosing the best HIPAA-compliant video conferencing solution is vital to prevent such breaches.
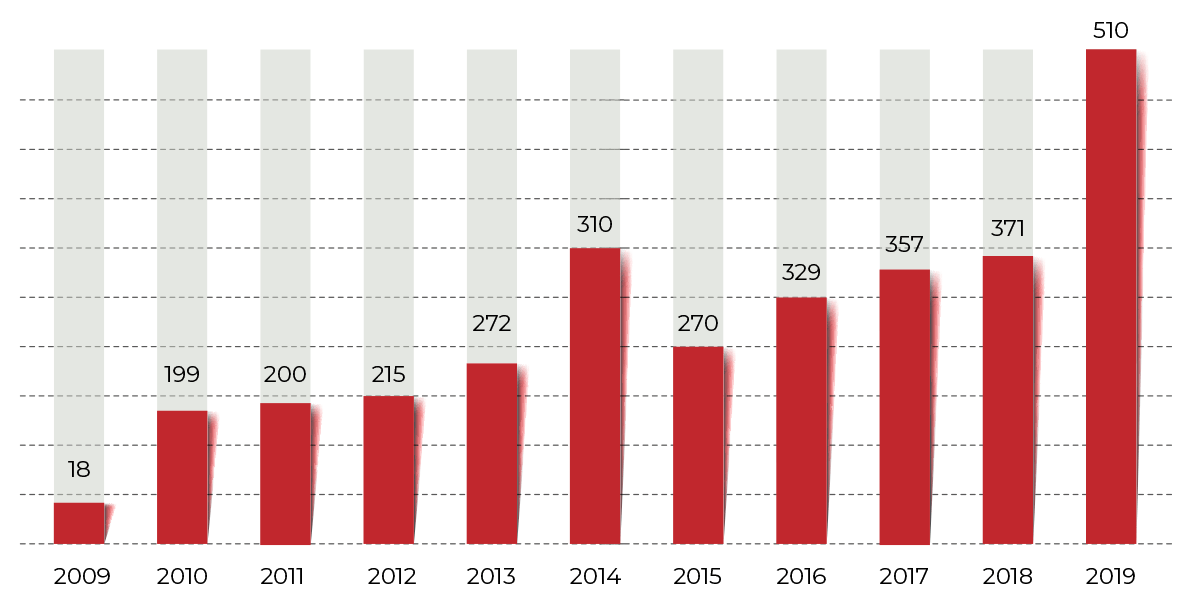
Healthcare data breaches of 500 or more records
Source: HIPAA Journal
For telemedicine video conferencing to be adopted successfully, meeting HIPAA-compliant video conferencing technology requirements is paramount.
How to ensure HIPAA-compliant video conferencing
Just like in the doctor’s office, online consultations must remain private and confidential. But the use of digital channels in telemedicine entails new privacy and security challenges — video and audio calls, session recording and storage, screen sharing, and medical files exchange. To ensure HIPAA-compliant WebRTC app development, let’s discuss compliance components and requirements in more detail.
How we can help
Experts in secure and highly scalable real-time communication, we deliver game-changing telemedicine video conferencing solutions to expand the reach of healthcare and drive better outcomes. By leveraging industry-standard streaming protocols and our low latency know-hows, we empower healthcare professionals to deliver the right care at the right moment. To ensure enterprise-grade security, we implement robust protective features like end-to-end encryption, biometric authentication, and more for airtight privacy and HIPAA compliance.
Strong access control
To prevent unauthorized access, HIPAA prescribes implementing measures that would allow access only to those who have been granted the respective rights and in the scope necessary to fulfill their job functions.
There are different technical measures available to control access. One of them is unique user identification. Assigning a unique name and number allows identifying and tracking users even when they switch devices to ensure that only persons with relevant permissions can access ePHI.
Other measures include role-based access control (RBAC) that helps segment users by roles and set up granular permissions and privileges to effectively manage access in your video conferencing solution. Encryption and decryption, though noted as addressable in HIPAA guidelines, must be implemented to guarantee that no one other than the receiving party can decipher and view protected health data. Security best practices dictate using 256-bit AES encryption, an industry-grade standard that ensures end-to-end protection of all in-meeting data.
Person or entity authentication
A backbone of any security strategy, strong authentication means verifying that a person or entity is what they claim to be before granting access to ePHI. Passwords paired with biometric authentication, such as facial recognition or fingerprints, add an extra layer of security to secure HIPAA-compliant video conferencing platforms. Biometric authentication is both effective and accurate, ensuring that only authorized users can access patient data.
The safest method of authentication is the one that leverages biometric information like facial features, irises, fingerprints, voice, or keystroke behavior. Unique and difficult to steal, biometrics deliver effective accuracy and streamline identification process while enabling HIPAA compliance of your telemedicine video conferencing solution.

Biometrics-based authentication
Leverage our expertise
Throughout years, we have been honing our expertise in machine learning and computer vision to help businesses create sustainable competitive advantages. Our deep and machine learning know-hows underpin state-of-the-art biometrics solutions that leverage facial recognition, voice biometrics, fingerprint recognition, and keystroke dynamics to ensure robust and reliable authentication across platforms and devices.
Harness the power of biometrics to secure your telemedicine platform.
Data transmission security
In a telehealth session, confidential ePHI is exchanged between the participants through video and audio calls, desktop share, and other means of collaboration. When moving, this sensitive information is at its most vulnerable as it is exposed to multiple risks, including MITM attacks.
Using AES-based algorithms ensures end-to-end encryption and protection of data both at rest and in transit. Also, to protect communication privacy, a telemedicine video conferencing solution needs to leverage Secure Real-Time Transport Protocol (SRTP) for safe exchange of all telehealth call data between browsers without interception.
Integrity
Under the Security Rule, healthcare providers must undertake measures to ensure that ePHI is not altered or destroyed in an unauthorised manner as compromised health data can result in patient safety issues.
Implementing strong end-to-end encryption guarantees data protection from alteration or tampering when ePHI is transmitted during a telemedicine video conferencing session. To corroborate data integrity, relevant processes and procedures must be in place that may include digital signatures, checksum verification, and more.
Activity logs and audit controls
In a highly regulated healthcare industry, detailed activity logs and audit trails must be presented for all systems using ePHI. By logging key actions, access threads, modifications, and more, these audit logs are instrumental in detecting security violations and unauthorized access to protected data.
To create a complete audit trail, all details of a video conference session need to be captured, including video, audio, and metadata. Since this granular auditing generates massive amounts of data, make sure your telemedicine solution’s analytic capabilities are adequate to process large volumes of information, identify suspicious patterns, and deliver granular audit reports.
Wrapping up on HIPAA compliance
In a world where healthcare resources are limited and health spending is on the rise, telemedicine emerges as an effective way to deliver high-quality patient care for a fraction of the cost. But just as telehealth adoption grows, so are the privacy and security issues these new connected health solutions bring.
Since telemedicine deals with sensitive health data, strong HIPAA compliance is a must to address a patient’s privacy concerns and deliver the same level confidentiality as for in-person visit. End-to-end encryption, granular access control, biometrics-based authentication, and robust audit controls are prerequisites for a HIPAA-compliant telemedicine video conferencing solution.