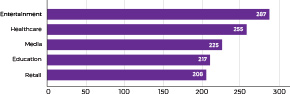
Today, IoT devices have become an essential part of the healthcare industry. Experts estimate that U.S. hospitals possess around 10-15 millions of smart healthcare devices. While we allow the gadgets to make use of our sensitive patient data, many of us don’t fully trust them.
Asking why? The majority of healthcare devices are very poorly protected, still relying on legacy security systems and old-fashioned data protection algorithms.
Tap into our IoT experts’ tips to bolster the security system of your healthcare software solution and prevent breaches proactively, rather than regularly waste your time and money on data security firefighting.
Must-Do Operations to Minimize Breaching Risks
Work Out a Device Security Strategy
First things first: you need a clear device security strategy, including a backup-based recovery, device behavior monitoring, network segmentation, authentication rules, and more.
To effectively protect users’ ePHI, your cybersecurity strategy must also be standards-compliant, including HIPAA, GDPR, FDA, and more.
Build a Proactive Monitoring System
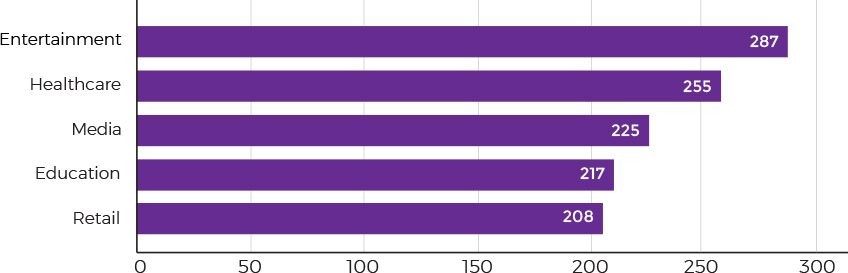
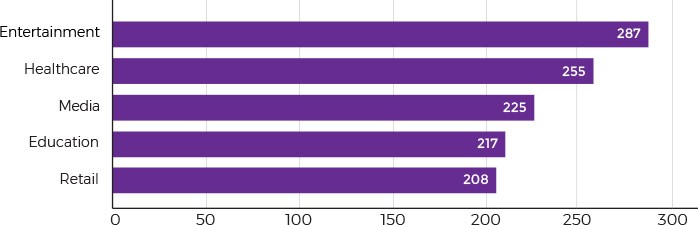
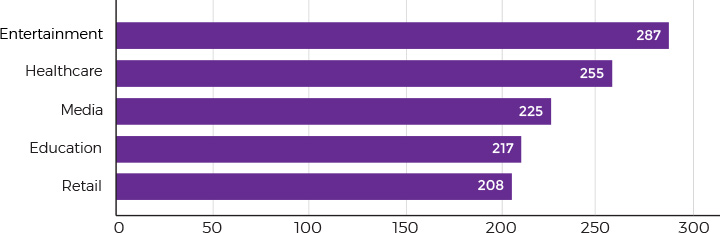
Even though continuously tracking all your IoT devices may sound rather difficult, it’s the only chance to identify and handle a data breach until something dreadful happens. Advanced device activity monitoring and early anomaly detection allows you to identify threats in as little as 3.5 hours versus the industry average of 255 days. Consider integrating with a cloud-based platform or building your own monitoring system to analyze abnormal device behavior and suspicious network activity.
Average time to identify a data breach by industry (Source: Ponemon Institute Cost of a Data Breach Study 2018)
Maintain a Secure Backup for Disaster Recovery
It’s almost impossible to protect your system from breaching once and for all. However, if a breach occurs, you will need a clear recovery plan to minimize the harm done to your users’ data.
The core element of a quick recovery is a solid backup strategy. A well-tested backup and restore procedure will be instrumental in reducing the time to contain a data breach and dramatically minimizing data loss and patient care interruption.
For maximum availability and reliability, encrypt your backup copies and store them in secure off-site storage.
Educate Your Staff and Users on Cybersecurity
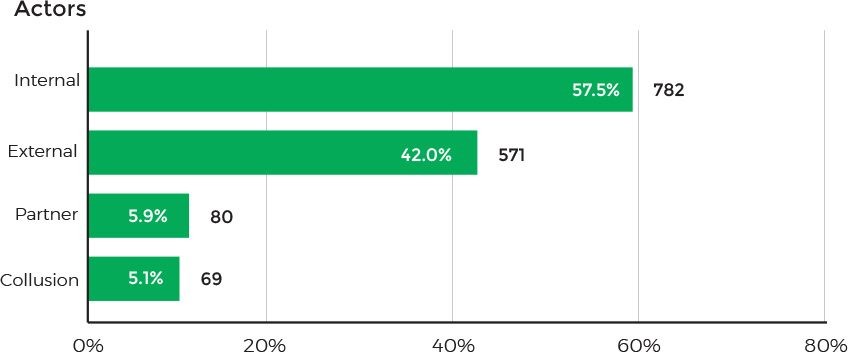
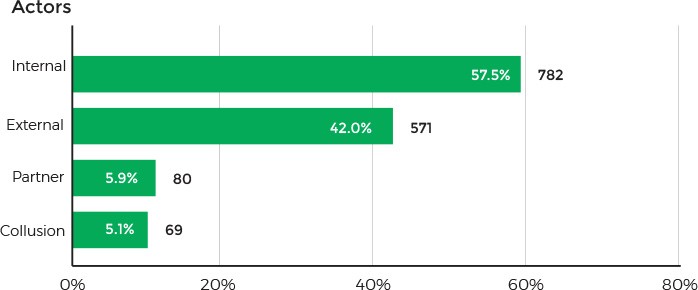
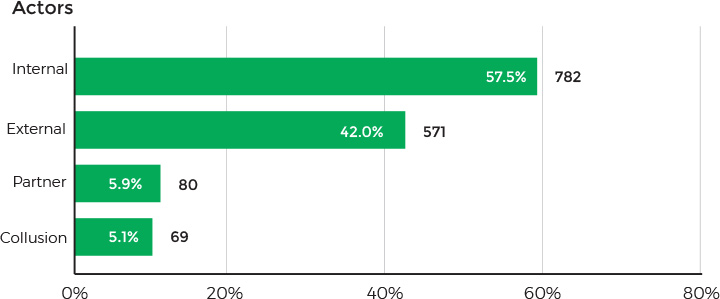
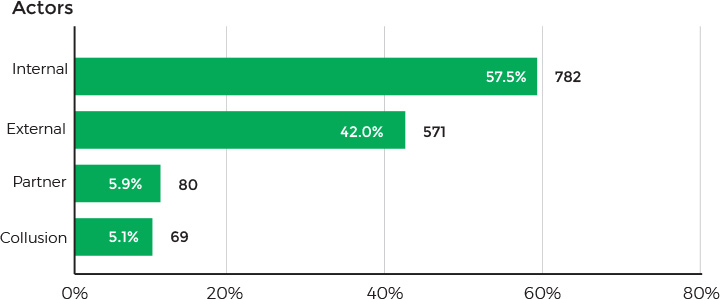
In terms of data security, healthcare remains the only industry in which employees and clients pose the greatest threat to an organization. According to Verizon, 57.5% of data breaching incidents involved insiders.
Source: Verizon 2018 Protected Health Information Data Breach Report
Whether you are a device producer or an IoT healthcare company, it is essential to train your personnel and clients upon the list of the most important security rules. Investing very little effort to avoid almost two-thirds of all the security incidents is certainly worth trying, isn’t it?
Security rules for the users of your IoT healthcare devices:
- Always use a strong password
- Give full respect to the multi-factor authentication
- Never access non-password-protected public networks with your healthcare device
- Treat each Wi-Fi network as potentially insecure
Physical Tampering: 3 Tips to Keep Your Devices Protected
Restrict Unauthorized Physical Access to Healthcare Devices
- Ensure your devices have no exposed ports or connectors
- Install smart locks and CCTV to prevent unauthorized access to the devices
- Make sure your custom healthcare applications communicate only with approved devices
- Forbid devices to access public unpassworded Wi-Fi networks
However, it’s impossible to control physical access to personal medical devices 24/7, which means you have to bolster two other layers of defense: a multi-factor authentication and on-device data encryption.
Security Rules for personnel:
- Don’t access any sensitive data without a lawful business purpose
- Don’t connect your personal devices (USB drives, external hard drives, etc.) to the organization’s network or any exposed ports of the medical equipment
- Don’t use organization’s or client’s medical devices for your personal needs
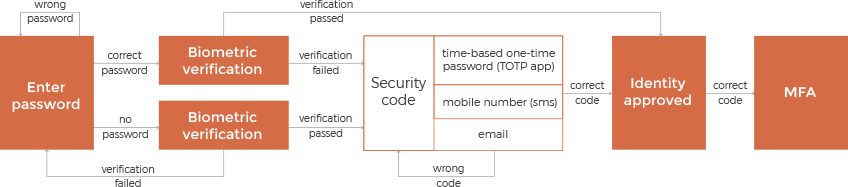
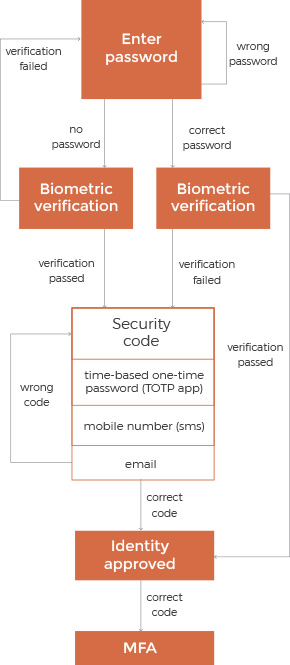
Use Multi-Factor Authentication
An old-school login-password model isn’t secure enough for devices which manage private patient information — 63% of confirmed data breaches involve weak, default, or stolen passwords.
Multi-factor authentication may be key to ensuring that personal data on devices is secure and no one but the device owner can access it. In addition to a password, multi-factor authentication demands an owner’s fingerprint, time-based one-time password, or token. Even if the password is stolen, multi-factor authentication would prevent a thief from breaking in. Additionally, incorporating a password manager can ensure the creation and storage of complex, unique passwords for each device and account, enhancing overall security and reducing the risk associated with weak or reused passwords.
Implement FDE on Your Medical Devices
The HIPAA Security Guidelines strongly recommend (in fact, demand) encrypting patient data both in transit and at rest. One of the most effective ways of automated on-device data protection is full disk encryption (FDE).
As the name suggests, an entire device memory is encrypted at the factory or upon later firmware update. After being uploaded into the memory, data got encrypted automatically and a user can access it only with a master password. Even if the device is stolen or lost — the user will have enough time to remotely wipe or lock it.
Cyber Threats: Secure Your Devices against Mass Data Breaches, DDoSing, and Other Attacks.
Segment Device Network
Some device ecosystems still integrate all the company’s medical equipment, employees laptops, and client’s wearables into the same network. Therefore hackers need only DDoS the most vulnerable device to infiltrate the organization’s LAN and gain access to patient records, employee information, and more.
The most effective way of avoiding such a scenario is to segment your network. Network segmentation ensures that IoMT equipment is not connected to the same network as employees devices and organization data servers. In such cases, a DDoS attack cannot affect the whole network but a single device, which significantly reduces the risk of a mass data breach.
If your ecosystem includes hundreds of device types and you want to monitor and control their security in real-time — try implementing micro-segmentation. By using specialized automated tools, you create a dedicated network segment for each medical device type and make each network port serve as an authorization barrier.
Update On-Device Software Continuously
The advice is to keep your devices updated and patch security vulnerabilities as fast as possible. Sounds a bit like “Captain Obvious advice”, but you may be surprised at how many IoT healthcare companies neglect such a simple rule. Remember the WannaCry cyberattack, when almost half a million devices were infected? All these computers weren’t updated, even though the necessary patch had been released 2 months before the incident.
Obviously, no hospital or person wants to waste time manually updating their devices, let alone replace their perfectly-functioning medical equipment yearly due to security issues. As a medical device producer, you need a perfect plan on how to patch your devices without compromising the client’s experience and loyalty. As a first step, consider implementing an over-the-air update capability, which nowadays is the gold standard for IoT devices.
Another advice is to test your equipment continuously. Engage your QA team from the prototyping phase, test your device permanently, identify vulnerabilities and patch them. If you don’t have an in-house software QA team — outsource one. The sooner you start testing, the more security breaches you can prevent.
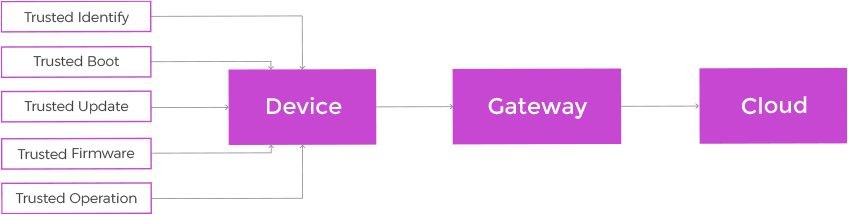
Integrate Your Devices with Secure IoT Cloud Platform
Designing a functional security system from scratch is no easy task — you need a cryptography-literate team, perfectly architected infrastructure, battle-proven security protocols, and more. However, there is a way of leveraging all IT security best practices without investing an arm and a leg into your own cryptographic empire. Integrate your IoT solution with major HIPAA cloud hosting platforms — like Atlantic.Net, Google Cloud IoT or IBM Watson IoT — that provide a full range of data protection services:
- Streaming data to the cloud via protected gateways
- In-transit data encryption
- Secure data storage
- Reliable backup services
- Powerful authentication and authorization APIs
- Protected communication across the ecosystem.
Bolstering Defenses to Handle Data Breaches Gracefully
In the end, cybersecurity is not about multiplying layers of defense and atomically segmenting your device network but about the safety of your users’ sensitive data. While we cannot eliminate breaches for good, continuously optimizing security will certainly minimize the risks.
Maintain a monitoring system, make frequent backups, keep your on-device software up-to-date, and continuously care about your patients’ security in all the other possible ways. And if the breach occurs — make sure that your patients are safe, and then handle it swiftly and effectively.
Oxagile synergizes multidomain expertise across data security, IoT development, and healthcare to ensure top-class breach protection for your medical ecosystem. Drop us a line if you need any help with security challenges in your IoT healthcare projects.