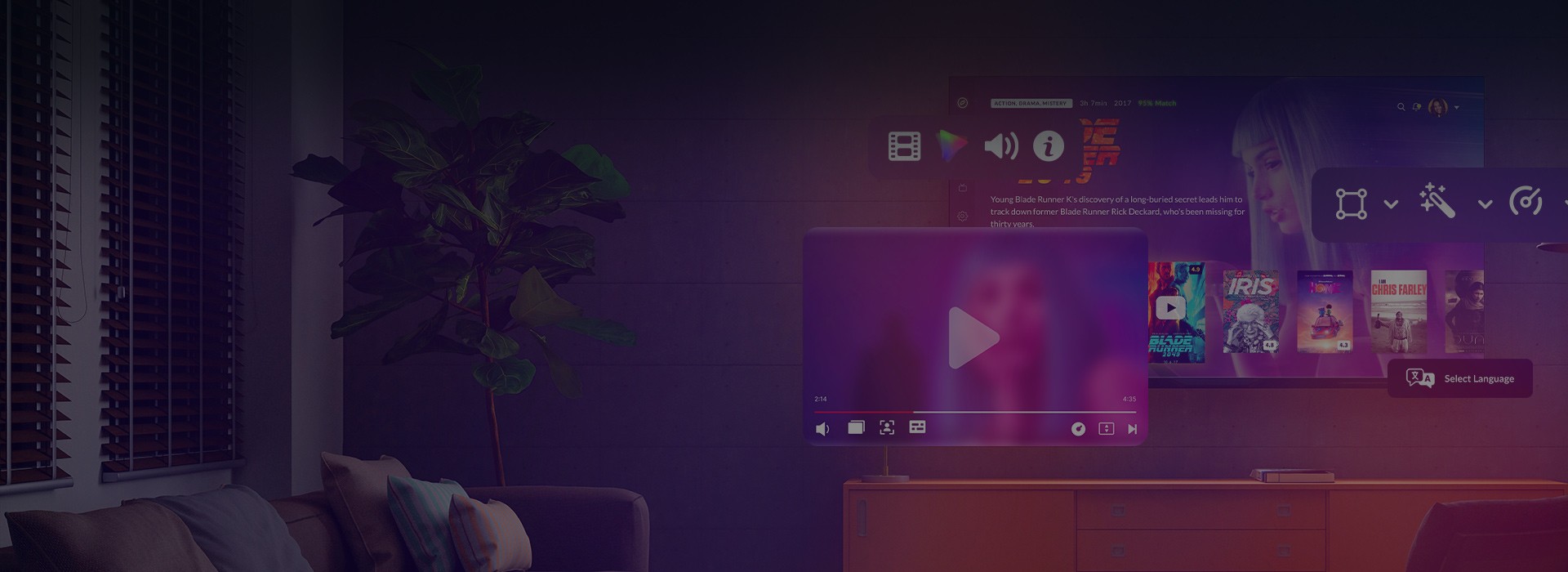
Outstanding UX and UI
- User-centric analysis and journey mapping
- Rapid wireframing and prototyping
- Clean, captivating, pixel-perfect UIs across platforms
- Easy user onboarding and intuitive navigation
- Stunning animations and effects
- Leveraging guidelines by Google and Apple, as well as the Carbon design system
- A/B and multivariate user behavior testing